How to Become an Information Security Analyst: A Guide for Beginners
We’ll cover what you need to know about becoming an information security analyst, from the different roles available to the types of education.

We’ll cover what you need to know about becoming an information security analyst, from the different roles available to the types of education.
Cybersecurity focuses on protecting the system as a whole, while information security protects the data within the system.
![Malware vs Phishing – Types of Cyberattacks [Infographic]](https://smartwalrus.com/wp-content/uploads/2023/03/Malware-vs-Phishing-Feature-300x169.jpg)
Malware vs phishing – Learn about the types of cyber attacks. What is it? What does it do? What are examples? And how is it prevented?

With cyber attacks on every level, from government to small businesses, the demand for information security professionals is at a high.

Here are five steps to help you train your employees in cybersecurity, reduce cyber threats and can ensure your business is safe and secure.
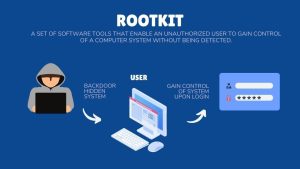
A rootkit attack is a type of cyber attack that uses specialized software to gain access to a computer or network’s core operating systems.
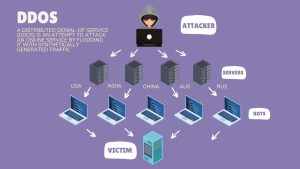
A distributed denial-of-service (DDoS) attack disrupts a targeted server, service, or network by overwhelming the target with traffic.
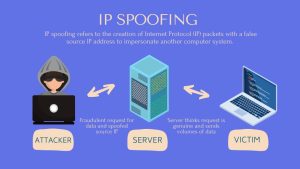
IP spoofing involves the manipulation of source IP addresses in network packets to hide the originator’s identity or impersonate a system.

DNS spoofing (DNS cache poisoning) is an attack that manipulates the Domain Name System (DNS) to redirect users from one website to another.

A man-in-the-middle attack (MITM) is a cyberattack where they secretly inserts themselves into a communication session between two parties.