What Is a Rootkit Attack?
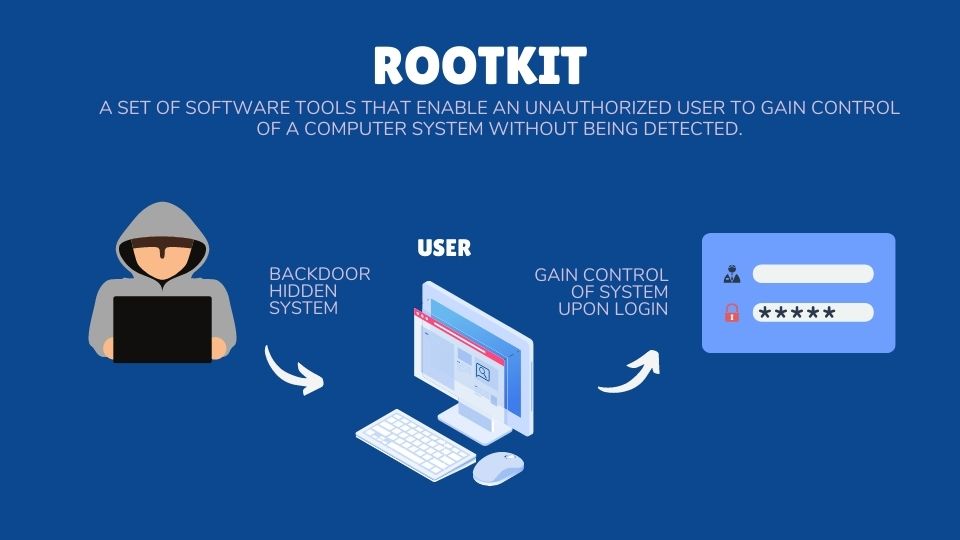
What is a Rootkit?
A rootkit attack is a type of malicious cyber-attack that uses specialized software to gain access to a computer or network’s core operating systems and applications. Rootkit attacks are particularly dangerous because they are difficult to detect and can continue to remain undetected for long periods of time.
Rootkits enable an attacker to gain privileged access to the system and remain in control even after the initial attack. This allows the attacker to perform various malicious activities, such as spying on users, stealing data, modifying system files, and launching additional attacks. Rootkits can also be used to infect other computers on the same network, creating a foothold for further malicious actions.
What are the dangers of rootkit attacks?
Rootkit attacks are typically stealthy and can be difficult to detect as they often use various techniques to hide their presence on the system. With a successful rootkit attack, an attacker can gain control of a system and have the ability to perform a wide variety of malicious activities.

These activities can include stealing sensitive data, installing additional malicious software, creating backdoors for remote access, conducting reconnaissance, launching denial of service (DoS) attacks, and much more.
In addition, rootkits can be used to disable security features, modify system configurations, and change system settings in order to gain further access. Because of the potential damage rootkit attacks can cause, it is important for organizations and individuals to take steps to prevent them from occurring.
How to prevent rootkit attacks
Rootkit attacks are a type of malicious attack that can be difficult to detect and even harder to prevent. In order to protect yourself against rootkit attacks, there are several steps you should take:
By following these steps, you can help ensure that your system stays safe and secure. Don’t forget to learn more about other types of attacks like MITM attacks, DNS spoofing, DDoS attacks, and IP spoofing.

Related Cybersecurity
How To Train Your Employees in Cybersecurity
What is a Distributed Denial-of-Service (DDoS) Attack?
3 Key Skills To Be a Cybersecurity Analyst
What Is DNS Spoofing?
What Is a Rootkit Attack?
7 Types of Cybersecurity Careers
What Is a Man in the Middle (MITM) Attack?
How to Become an Information Security Analyst: A Guide for Beginners