What Is a Man in the Middle (MITM) Attack?
What is a Man in the Middle (MITM) Attack
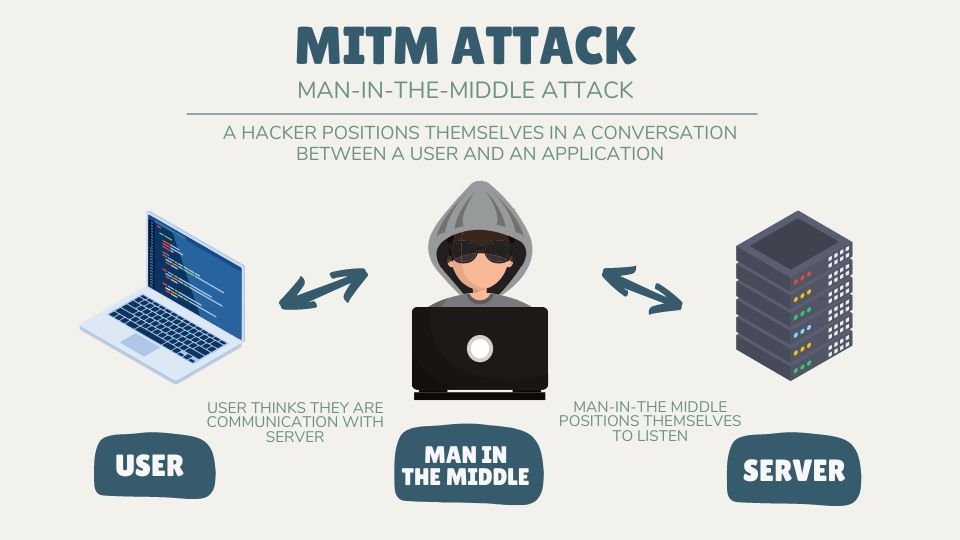
A man-in-the-middle attack (MITM) is a type of cyberattack where an attacker secretly inserts themselves into a communication session between two parties. This allows the attacker to intercept, monitor, and modify data being exchanged between the two parties.
In addition, the attacker can steal confidential information or gain access to sensitive accounts. The attacker is able to monitor the communication, pose as either party and even manipulate the data that is being exchanged.
The Anatomy of a MITM Attack
Man-in-the-middle attacks are often difficult to detect because they don’t leave any trace of their presence on the network. Furthermore, these attacks often rely on social engineering techniques to lure unsuspecting users into trusting the attacker.

These types of attacks are particularly difficult to detect because the malicious actor can manipulate traffic in such a way that it appears legitimate. This can be done by spoofing IP addresses, impersonating a trusted source, or manipulating data in transit.
Additionally, the malicious actor may be able to hide their malicious activity by using encryption or obfuscation techniques. Furthermore, in many cases, the malicious actor is able to gain access to the network without alerting the victim or the organization. Similar to a botnet cyberattack, they can steal valuable information from infected devices.
How To Protect From a MITM Attack
In order to detect MITM attacks effectively, organizations need to have robust security measures in place, such as advanced monitoring and detection systems, strong authentication protocols, and an understanding of the typical communication patterns for their network.
There are a variety of methods used to protect against man-in-the-middle attacks. These include:
Additionally, organizations need to continuously monitor their networks for any suspicious activity and take immediate action if any suspicious activities are detected. Organizations should also ensure that their security measures are kept up to date with the latest security threats and that their users are educated on the risks associated with online activities.
In addition, users should always be aware of suspicious emails, links, or requests for personal information from unfamiliar sources. Users should be trained on cybersecurity and the existing threats in the cybersecurity landscape. Learn more about other common threats like botnets, DNS spoofing, DDoS attacks, IP spoofing, and rootkit attacks.

Related Cybersecurity
What is a Distributed Denial-of-Service (DDoS) Attack?
5 Reasons to Consider a Career in Cybersecurity
What Is DNS Spoofing?
Malware vs Phishing – Types of Cyberattacks [Infographic]
How To Train Your Employees in Cybersecurity
What Is a Man in the Middle (MITM) Attack?
5 Cybersecurity Career Tips for Beginners
7 Types of Cybersecurity Careers